Alessandro Stesi
Alessandro Stesi
Help Folding@home project with Secure Online Desktop
Folding@home is a distributed computing project for simulating protein dynamics – the process of protein folding and the movements of proteins implicated in a variety of cancers and diseases, including Alzheimer’s, Ebola and COVID-19.
By enabling people across the world to run these simulations on their personal computers, the Folding@home project aims to help scientists better understand these processes and identify new opportunities for treatments.
Of course, you can run Folding@home as a virtual machine in an Secure Online Desktop cloud too. The Folding@home client is available in the Secure Online Desktop template library, so every Cloud Server users can use it to build their Virtual Machine. Here’s a quick guide to setting it up.
1. Build a virtual server using the Folding@home template
To get started, deploy a Virtual Server using this template. Modify CPU/RAM to your liking and build the VS.
Once the VS is up and running, ssh/console to VS and confirm that the fah service is running:
[root@folding ~]# /etc/init.d/FAHClient status
fahclient is running with PID 1268
Edit config.xml in /etc/fahclient directory and modify it to add the <!– Remote Command Server –> section, in which we can tell the client our remote IP address. Or do as I have done in this case, and allow access from all (0.0.0.0/0) but with a password:
[root@folding ~]# cat /etc/fahclient/config.xml
With above config added, restart the fah service:
[root@folding ~]# /etc/init.d/FAHClient restart
Stopping fahclient ... OK
Starting fahclient ... OK
2. Install FAHControl
Next we are going to install FAHControl to your local desktop or laptop PC. It’s a GUI for controlling one or more Folding@home clients. You can learn more and get the installer from https://foldingathome.org/support/faq/installation-guides/
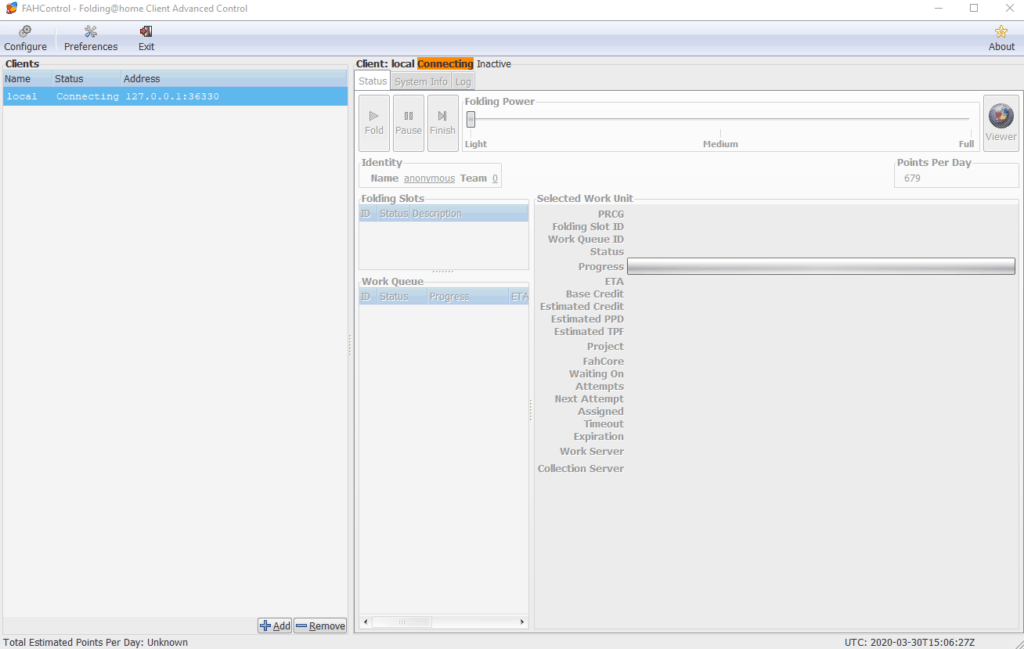
Once it’s installed, launch the application and you should see something similar to this:
Now we can add our client running on the VS we deployed in Secure Online Desktop. You will need the public IP address of the VS, and ensure that you can reach port 36330.
Click the small Add button towards the bottom of the FAHControl client, and provide the Display Name, Hostname/IP address and the password you set earlier.
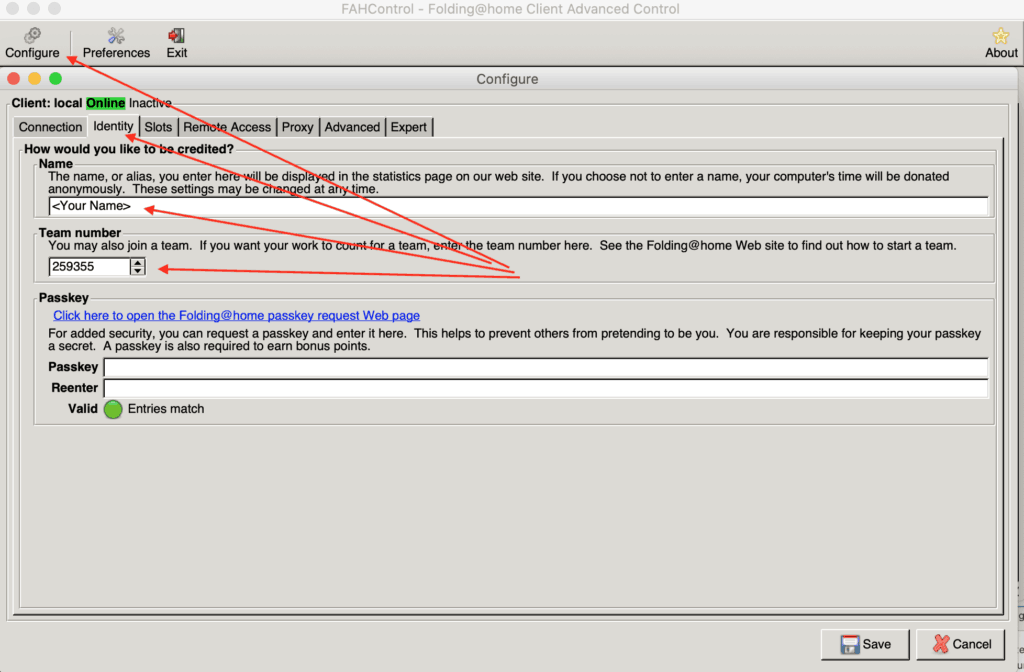
In the Configure section, under Identity tab specify your Name and our Team Number that is 259355 as reported below:
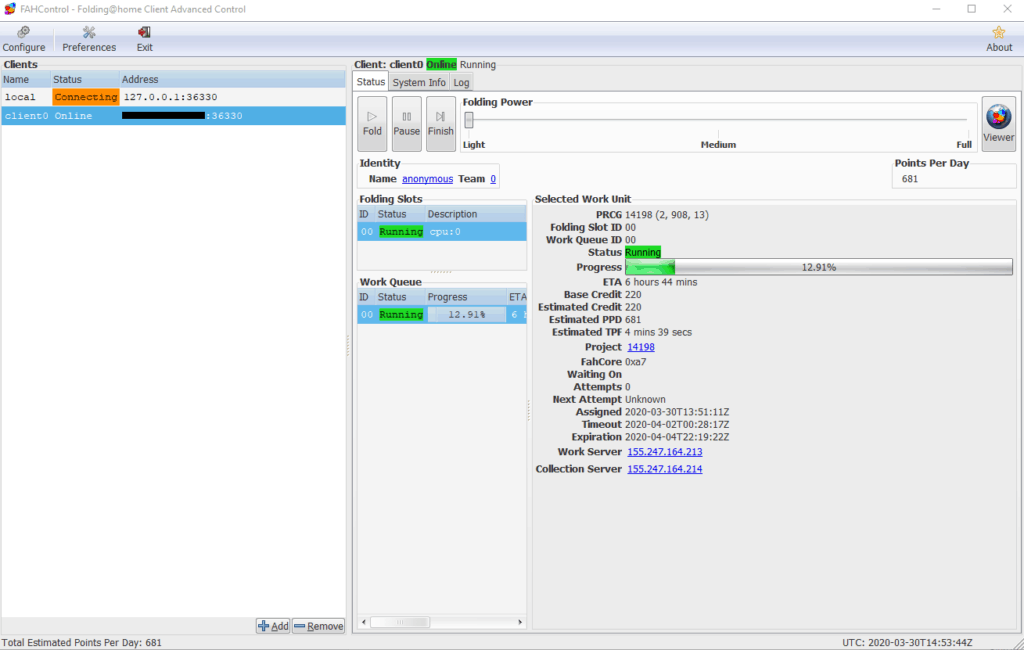
You should now see that FAHControl has connected and is working.
To find more details about how it works, and other information about the Folding@home project, visit https://foldingathome.org/.
You can check our Team stats here: https://stats.foldingathome.org/team/259355 including your contribute.
Please note that for help Folding@home project it is not mandatory to create a VPS on our Cloud, you can use your own PC to do that. The advantage to support Folding@home project via our VPS is that, despite your PC, you can leave the process running all time and for instance you can allocate free resources (like CPU and RAM) you have free in your Cloud Server or SuperCloud subscription.
[btnsx id=”2931″]
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO