 Giacomo Lanzi
Giacomo Lanzi
Free trial of internet services with Demos
The services provided by Secure Online Desktop are many and cover a large variety of needs. We realize that for the layman and the less experienced, this could be intimidating. In the midst of so much choice, how can we be sure that the service we need is exactly what we are about to request? For this reason, we provide our visitors with a free trial of the services, in the form of a demo.
What does free trial mean
By accessing the service demos, it is possible to test the real user experience without having to buy anything. Before we take action and show you how to access and use our demos, let’s clarify a couple of things.
The free trial refers to accounts made available to our visitors in a shared way. This means that by accessing the services under test, you access non-private environments. Therefore it is always better not to enter any sensitive information or files because they could be seen by other people.
It should also be remembered that the free trial accounts are regularly reset and all data within them deleted. This security measure is designed to limit the intervention of our technicians and to automate the cleaning of the environments offered with demo accounts.
Which Internet services can you try?
The services offered in free trial are of two types: one immediately available and another in which to access you will have to request free credentials by filling out a form on our site.
The services offered in free trial and immediately available are:
Web Hosting, Cloud Server (Windows and Linux), ICT Monitoring e OwnCloud.
The services that instead require sending a request for free credentials are:
Cloud CRM, Cloud Conference, Acronis Cloud Backup, Log Management and Cloud Desktop. To request any of the services, just visit the support page and contact us by filling out the form, requesting login credentials.
No sensitive personal data, no credit card registration or other payment methods are required. The test service is completely free and without obligation.
How to access the services under trial
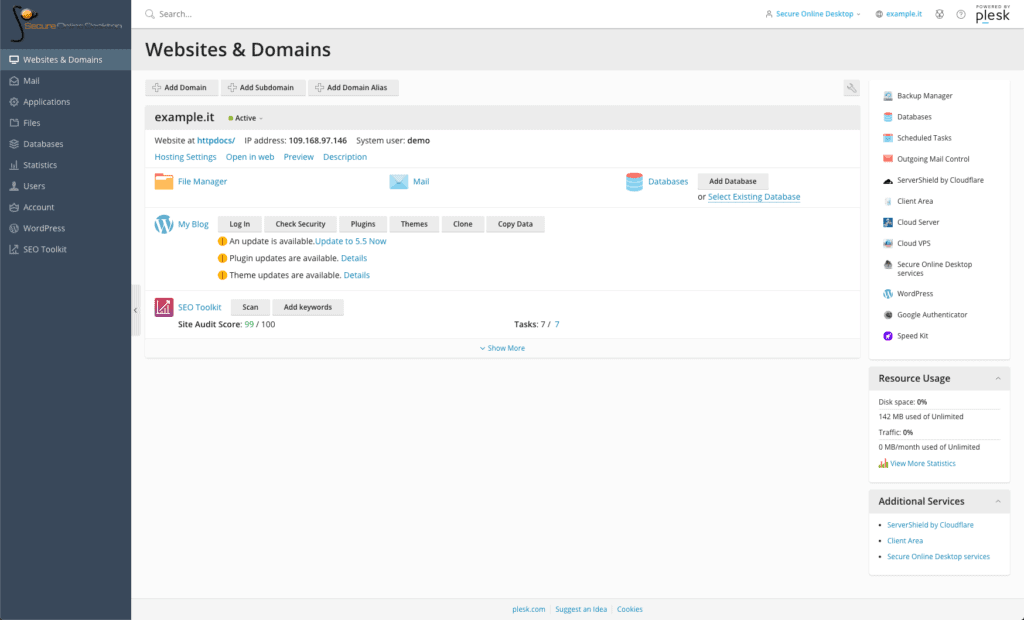
Web hosting
By clicking on the appropriate link, you immediately access the Plesk panel of the SOD Web Hosting service. From here it is possible to test many features using the side menu directly.
Among the possibilities are: modify the server parameters, check and access the installed database, change the version of PHP in use, try the SEO Toolkit and much more.
Always remember that the data entered can be seen by other users and that in any case they are deleted regularly.
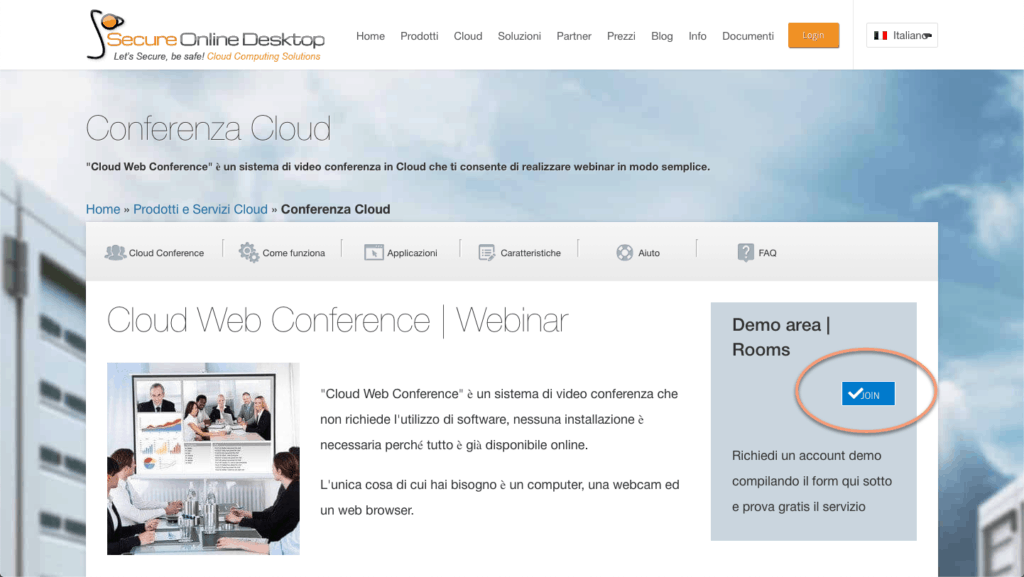
Cloud conference
It is possible to try this service in two ways. The first is by visiting his page and clicking on the “Join” button (only for registered users). In this way you access a virtual room in which to test the functionality. You will find yourself in a public room, where it is possible for other people to log in with the same intentions as you to try the service.
It is possible to request specific credentials to thoroughly test the service, perhaps using it with friends or relatives to verify all its features. To do this, you need to request credentials via the contact form.
Cloud Server
The free trial of the Cloud Server service is available on both Windows and Linux machines. After having landed on the service page, and clicking on the “login credentials” link of the Operating System you want to try, you will find yourself in a page where there are ip, username and password for access.
With these data, by inserting them in a Remote Desktop software, it is possible to test the service. To access the servers we recommend CoRD, a remote desktop management software for MacOS X, or Windows mstcs, a similar program for S.O. Windows.
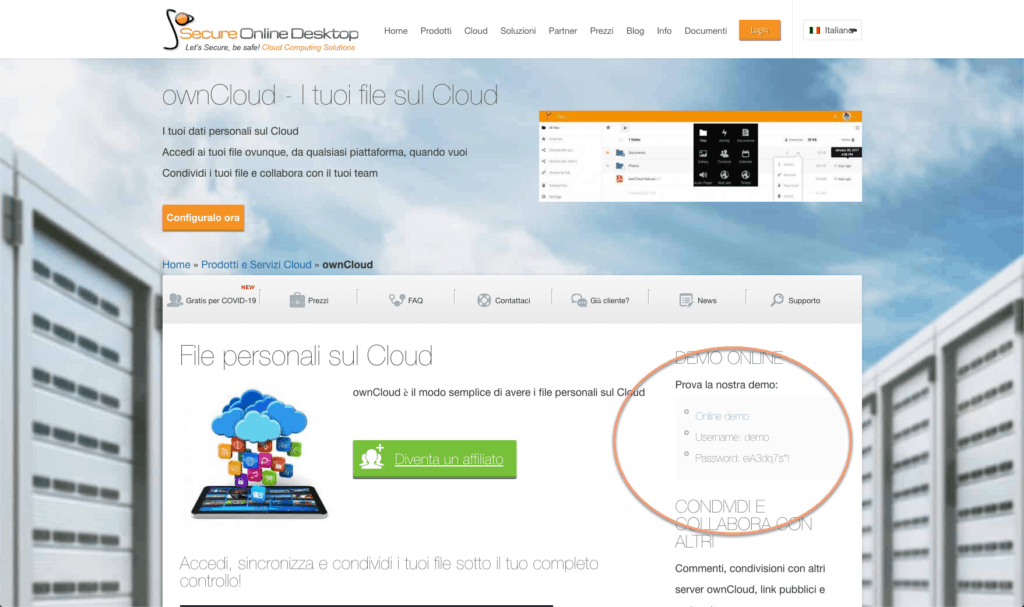
OwnCloud
To access the ownCloud service demo, the first thing to do is go to the service page. At the top right you will find the credentials for the free trial and a link to the service panel.
Once you click on the “Online demo” link, you are asked to enter your credentials to access the panel.
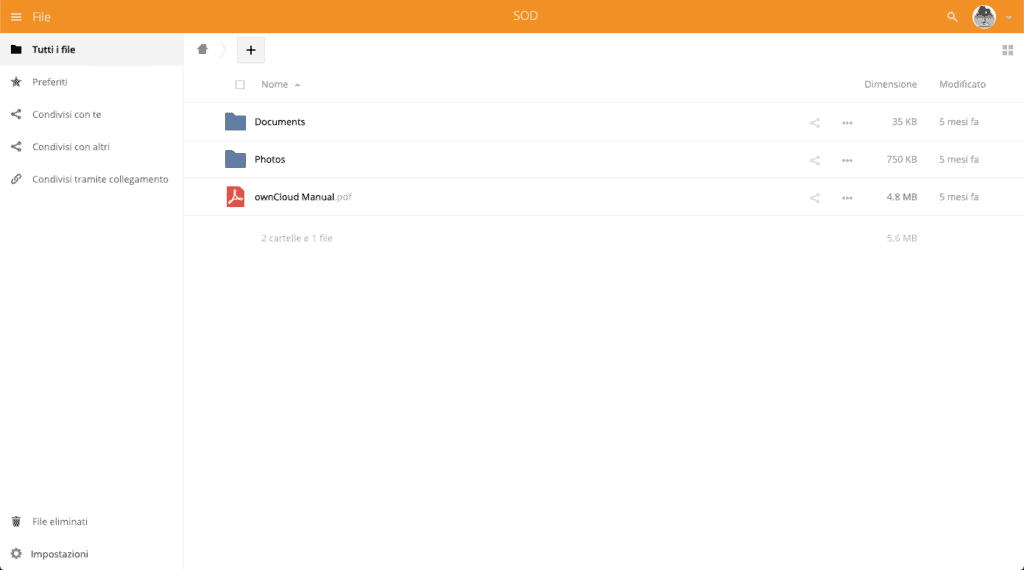
Once logged in, you can take advantage of the free trial. In the central part of the panel, the items present in the root of the storage space are listed. It is possible to find a manual in pdf and two folders containing example files of type odt and jpg. All these files can be viewed inside the panel using the integrated tool.
Remember that even in this case, the service resets itself every 24 hours, deleting any file that has been uploaded, moreover, any file that is uploaded can also be viewed and possibly downloaded by anyone who accesses the demo.
ICT monitoring
To access the free trial of the ICT Monitoring service, you can go directly to the page https://monitor002.cyberfero.com/zabbix and enter the word demo as user and password.
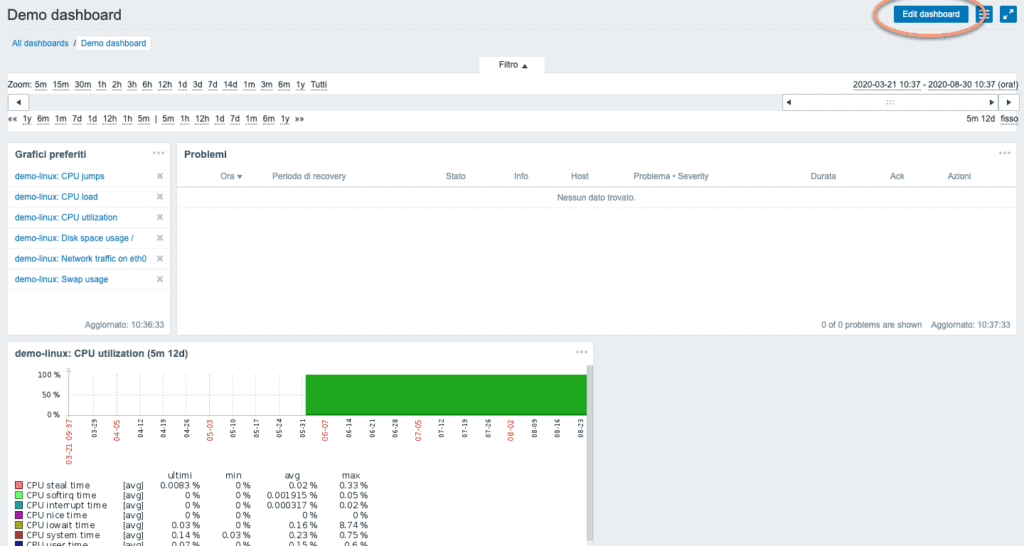
Once logged in, you can interact with the dashboard where the status of the IT system is represented at a glance. The widgets containing the visible information can be customized by number and data shown. Just click on Edit Dashboard, at the top right. A menu will open from which you can choose the source and type of values shown.
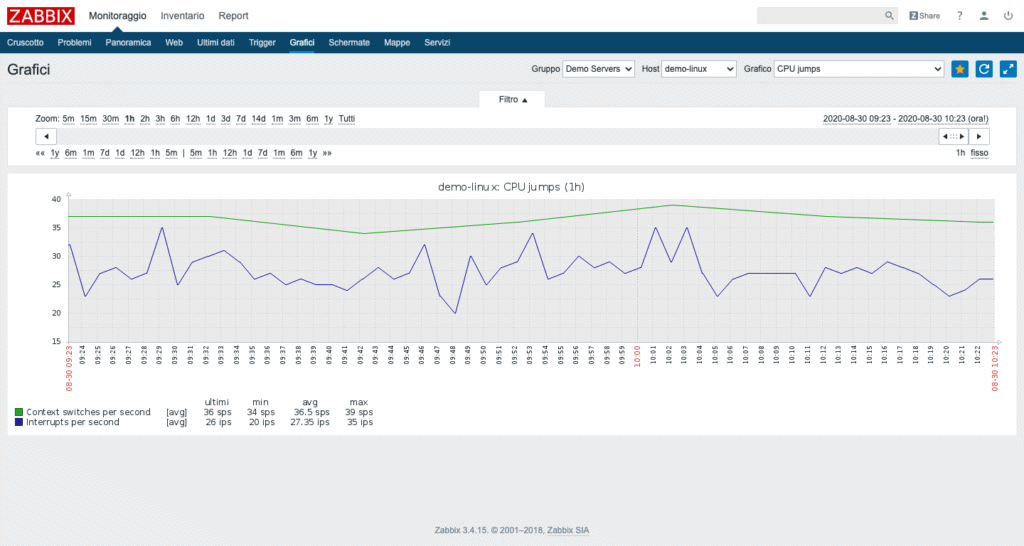
It is possible to access, from the dashboard menu, specific pages, such as those containing the graphs or the list of problems.
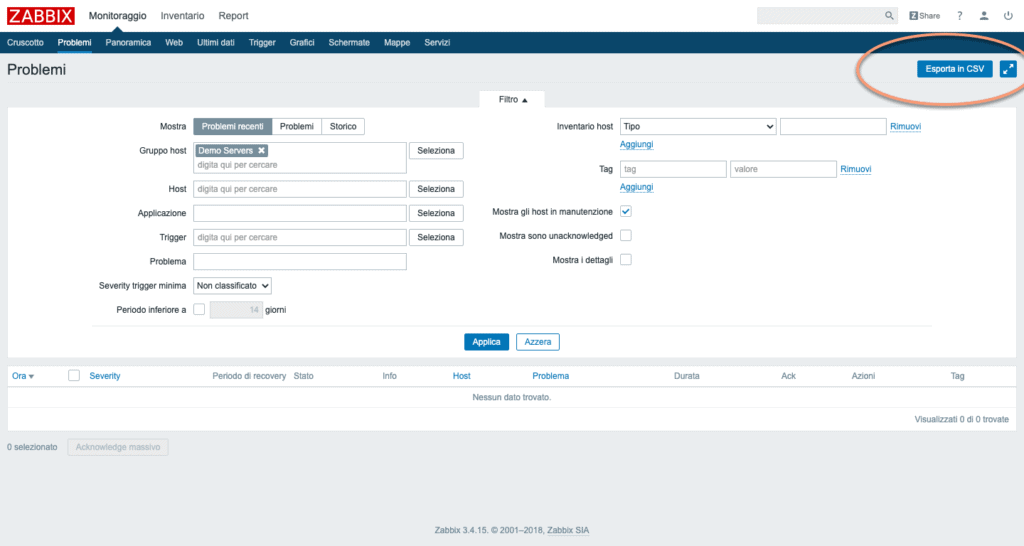
Each screen offers useful information for controlling the IT system. It is possible to filter the data shown and in some cases, as in the recent problems screen, even extract the values in CSV to analyze them in more depth and perform detailed analyzes.
Conclusions
The services offered by SOD are qualitatively very valid and cover a wide range of needs. If you are undecided about the service and would like to try it before buying it, you can do it freely. The free trial of our services does not require any credit card insertion, no fee will be applied and is not binding on the purchase.
The advice is to test the services and get in touch with us for any doubts, we will be able to answer your questions and offer you the best solution to your specific situation.
[btnsx id=”2931″]
Useful links:
Plesk CloudFlare estensione gratuita per gli utenti Webhosting
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO