 Giacomo Lanzi
Giacomo Lanzi
Quality certificate for the SOCaaS of SOD
Estimated reading time: 7 minutes
The technology we use to deliver our SOCaaS has been awarded a quality certificate . Today we want to talk about this, explaining again what a SOC is and why a SOCaaS is an ideal solution for companies.
Of course, we will also explain what it is about when we talk about the quality certificate and how this ensures excellent service for our customers.
Differences between SOC and SOCaaS
A SOC, acronym for Security Operation Center , is a central command hub that acquires data from an IT infrastructure and analyzes it. Ideally, all devices that are part of the infrastructure are part of the data collection. This means, in the business environment, that every device connected to the network or that connects to the network by accrediting itself, should be included in the data collection.
A SOC is a physical place, with hardware tools, where a team of IT technicians manage the data flow and analyze it using the available tools. This means maintenance, installation and employee maintenance costs.
A more flexible variant is represented by SOCaaS, ie Security Operation Center as a Service . It is a model based on services provided by an external supplier that delocalizes the tasks of a SOC. With the increasingly important evolution and diffusion of the cloud, we have come to a situation in which SOCaaS is the main driver. Thanks to cloud technologies, in fact, data collection and network information, as well as logs, can be reached via the network.
To simplify: a SOCaaS is a SOC, which however is provided as a service; in practice, the brain of the SOC is connected to the infrastructure to be monitored and not internal to the company. The costs of implementation, maintenance and management are greatly reduced.
Thanks to SOCaaS and automation and analysis tools, the environment you want to control is constantly monitored and threats and anomalies are detected in real time.
SOD and quality certificate
Threats on the net have evolved over time to become extremely sophisticated. They target targets that fail to recognize them in a timely manner , resulting in damage that can be data loss or even the ransom note .
SOCaaS, as mentioned, simply allows you to save time and resources by replacing the staff to be employed in the search for the various malware that are always lurking.
We are pleased to say that the technologies we adopt in SOCaaS have been awarded a quality certificate and are positioned in the magic quadrant of Gartner. Among the resources available in our SOCaaS, we mention SDL , SIEM and UEBA .
SIEM collects all events and information to be managed, enriching the data in the SDL so that they are easily analyzed. UEBA’s user behavior analysis is invaluable when a social engineering attack arises.
Artificial intelligence offers an important help to our SOCaaS as it analyzes threats and possible risks. Furthermore, the constant presence of an available team ensures security against all ransomware attacks.
The quality certificate that our technology has received occupies a place of Leader in the Gartner’s Magic Quadrant . Gartner is an institution that has established who the most important IT vendors on the market since 1979.
Quality certificate equals excellence
It is essential these days to have a good valuation when you are in a certain market sector. For example, on eCommerce sites it is common to find user reviews before making a purchase. However, no one really guarantees that the reviews are genuine. Similarly, technologies available on the net are not always as beneficial as they appear. The Gartner Magic Quadrant takes care of that.
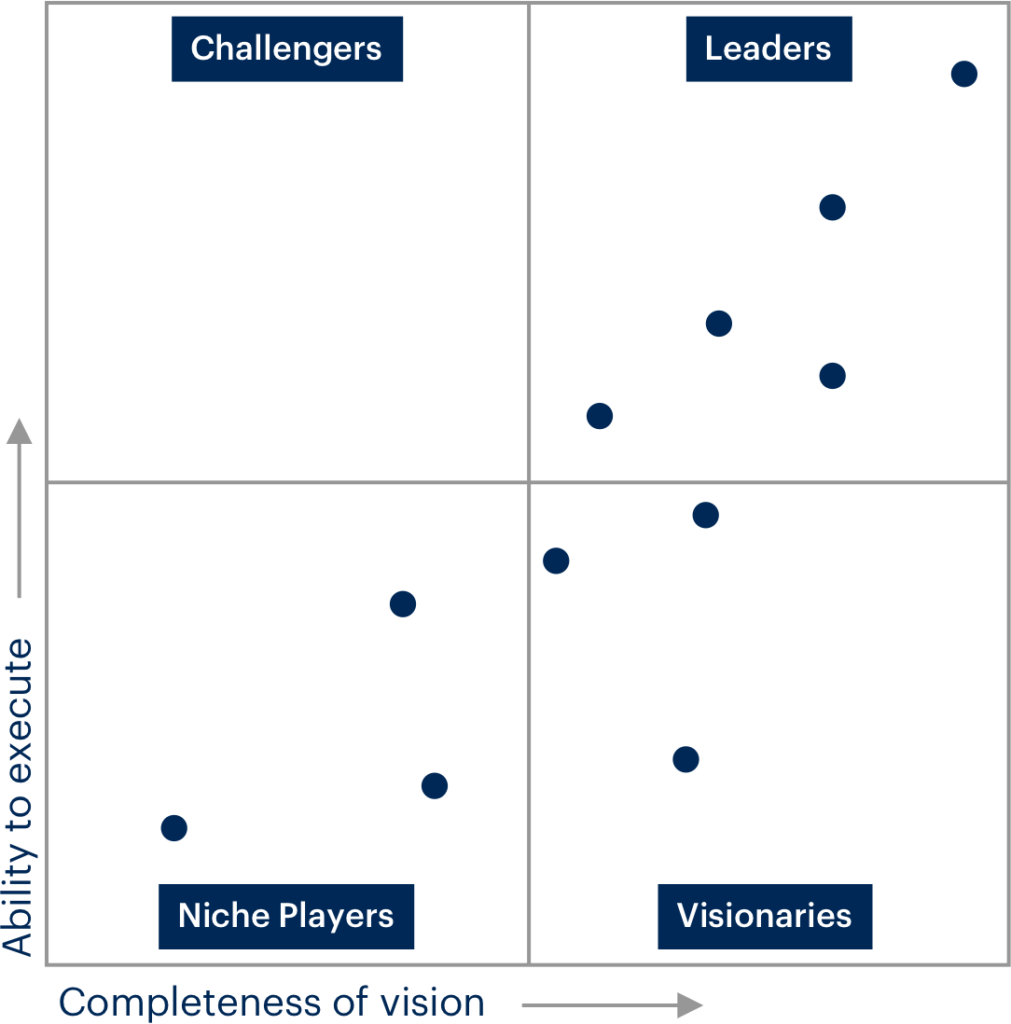
Gartner analyzes the players in the market for a service using qualitative analysis . Check the maturity, the participants and the market trends. The competition focuses on four aspects displayed in a graphical table, the so-called magic quadrant .
The quadrant is divided into categories: Visionaries, Challengers, Niche Players and Leaders. Most interest is directed towards the Leader position which represents the top for execution and completeness. Our technology is found right in the Leaders quadrant.
The Magic Quadrant offers almost immediate understanding of the most trusted providers on the market .
Obviously, there are various strategies to rely on when choosing a service or technology, and relying on Leaders is not always the best idea. What is good today may not be suitable in the future.
The alternatives could materialize in the market Challengers who move with speed or in the niche players who can guarantee a more precise and accurate service than a Leader.
Business objectives, in general, are the guide to follow and depend on your company but to be almost foolproof it is always better to ask for help from specialized companies able to provide advice and suggestions.
The magic quadrant of Gartner
As mentioned earlier, the Magic Quadrant is read using four parameters that need careful viewing. Below is a generic magic dial, while by clicking here you can see the list of all the magic dials divided by topic.
Leader
The supplier in the leading position has the credibility, market share and sales skills necessary for the distribution and acceptance of new technologies. Is able to understand the customer needs and always keeps an eye on innovation.
Sometimes he designs elaborate plans that he makes available to clients. In this way the infrastructures and strategies are efficient and feasible. From a financial point of view, it enjoys the stability and support of the platform, also thanks to the geographical coverage. This watch face can be defined as the real certificate of quality by looking at the magic dials.
Challenger
The greatest threat to the Leader is undoubtedly represented by the Opponent or Challenger. It works well and has a credible market position. The extreme faith in projects that can continually grow over time makes him capable of developing strong products.
While they are not as well established as the Leaders financially, they still remain stable and solid.
Visionary
The Visionary is perfect for all the novelties that could revolutionize the market. Such a supplier guarantees product innovation and is able to address operational and financial problems on a large scale.
One of the big flaws, however, is the instability due to unsustainable profitability and the ability to acquire market shares . Over time an investment can prove to be profitable or not but it basically depends on some signals that need to be interpreted.
The Visionary is often a private company or acquisition objectives by the more consolidated or large company because the possible risk probability of installing on their systems is lower in the event of an acquisition.
Niche operators or actors
The verticalization of the market or the focus on specific areas concerns all niche players. This supplier can be a large company but it is struggling to achieve the goal it has set or it is the one that adapts its product in order to enter a particular market.
In conclusion
Following your vision and establishing yourself online is never easy because it is not uncommon to encounter problems of various kinds, from a lack of resources to the difficulty of standing out on the market.
The technology we use for our SOCaaS has revolutionized the market and earned a place alongside the leaders in the Gartner Magic Quadrant. We are very happy with this milestone, which means better service for our customers, greater safety and in general the excellence we have always aimed for.
If you want to know how our services can help your business, do not hesitate to contact us, we will be happy to answer any questions.
Useful links:
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO