Alessandro Stesi
Alessandro Stesi
Subscription business model – Basics
subscription
Subscription is a convenient way to receive updates, products or services on a regular and ongoing basis. This business model has stood the test of time. Over the years, satisfied customers have used regular services by subscribing news, magazines, CDs, wine and even opera tickets. And then the cloud arrived. The cloud has made IT complex easy and cheap, thanks to the familiar service delivery subscription model.
Today, public cloud computing services have revenues of $ 246.8 billion. By 2020, Gartner says, cloud adoption strategies will affect over 50% of IT outsourcing contracts. Service providers are rushing to get on board.
Subscription
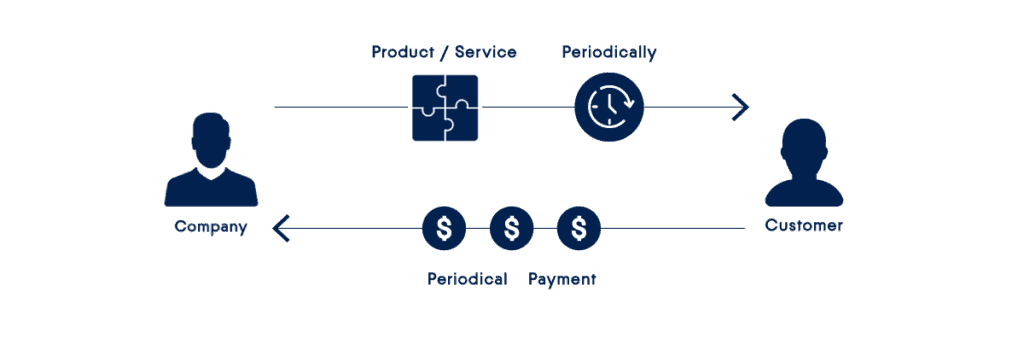
The subscription is an agreement to regularly receive products or services by paying in advance. It has become a default business model for service providers. Even those service integrators who have made their name by selling individual software licenses are currently switching to a subscription or a software-as-a-service service delivery method to stay alive and grow their customer base.
For customers, the subscription is based on practicality, scalability and economy. The consumption model of the OpEx-based subscription service beats the traditional CapEx model in all ways. Instead of spending hundreds and often thousands of euros on hardware devices and software licenses (and therefore worry about maintenance and upgrades), companies pay a manageable monthly fee just for what they use and only for the service they need.
Subscription models
There are two popular subscription models designed to attract new customers allowing them to try the service before engaging in a full subscription.
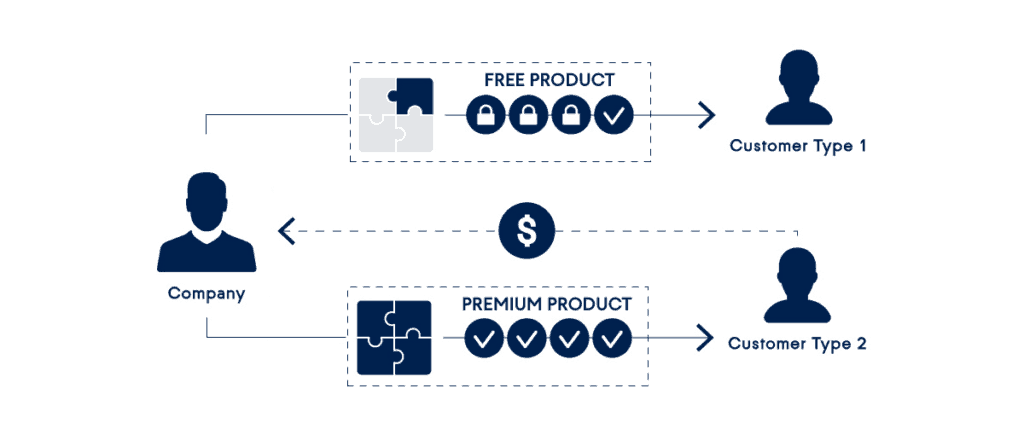
Freemium
A freemium business model offers a free basic service and additional paid features. This has become one of the dominant business models in the mobile app market and is widely adopted by cloud-based service providers. LinkedIn, Dropbox, Yammer and millions of other vendors have adopted this model, using free features as a powerful marketing tool. Users are more likely to direct the service to others when it’s free and easy to use. There are also signs that the freemium model is even more successful than the 30-day trial because it relieves customers from the cumbersome cancellation process when they are trying out the service for the first time.
As with the Acronis Cloud Backup service, the Freemium option allows you to have a free plan for a computer with local backup storage and then charge a fee for additional services such as cloud storage and other devices.
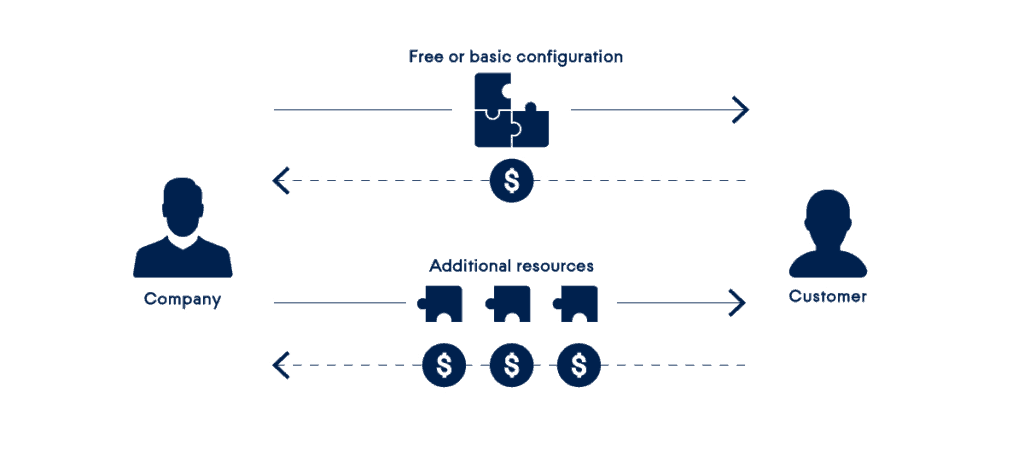
Bait and Hook
This subscription business model offers to offer a basic service at a low price, or even free, and to charge the full price for additional resources. The origin of this subscription method is often attributed to Gillette, a razor company that is known for selling cheap razor kits and expensive blade refills. Today this model is widely used by mobile phone companies (free telephone with a long-term service plan), printer manufacturers (cheap printers, expensive ink) and many other companies where most of the revenue comes from consumables .
With the Acronis Cloud Backup service, on the other hand, you have a free plan with a limited amount of storage space in the Cloud. This will allow customers to register and try the fully functional service before purchasing additional Cloud storage to meet their needs. In this section you can consult the complete list of demo services that Secure Online Desktop makes available to its customers.
Acronis Cloud Backup
The Acronis Cloud Backup service is specifically designed to meet the ever-increasing needs of customers oriented to the above-mentioned subscription models.
[btnsx id=”2931″]
Useful links:
A Hybrid Cloud Backup Solution for System Integrator and reseller
BaaS | Cloud Backup | Backup as a Service
New Acronis Cloud Backup model for end users and new reseller plan
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO