Backup as a Service
 Piergiorgio Venuti
Piergiorgio Venuti
Disaster Recovery Plan: Safeguarding the Future of Your Company
Today’s digital world is a dynamic and constantly evolving environment, where security and operational continuity represent not only a need, but a true imperative for companies of all sizes and sectors. In this context, a well-structured Disaster Recovery (DR) Plan is essential to ensure resilience and rapid response in the event of unexpected events and IT disasters. In this article,…
Ransomware and NAS: a risk that is not considered
Despite some seasonal declines, ransomware is still a serious security threat, especially for those who underestimate it . It is often thought that to protect yourself from ransomware it is enough to have a backup copy of your data. This point of view does not take into consideration various aspects. One of them is the relationship between ransomware and NAS…
 Giacomo Lanzi
Giacomo Lanzi
Avoid Ransomware: That’s why it’s best not to take any risks
ransomware gangs have been targeting businesses in recent times, demanding larger payments than they can extort from consumers. The plan was very successful. According to the new data, 70% of the attacked companies paid the ransom to get their data back. Avoiding ransomware is a necessity, these figures implicitly prove it. If such a large number of companies pay, it…
 Giacomo Lanzi
Giacomo Lanzi
Double extortion ransomware: What they are and how to defend yourself
Looking to up the ante and earn more money with the ransomware , i Cybercriminals are increasingly using a tactic known as double extortion ransomware . Not only do they encrypt data and demand a ransom from the victim to regain access. They also threaten to upload them online if their conditions are not met. Let’s take a step back,…
 Giacomo Lanzi
Giacomo Lanzi
The most dangerous Ransomware in 2020
The ransomware (or cyber extortion) threat is on the rise. In 2020, there was a spike in the number of reported incidents and the number of hackers attempting to extort money from organizations. It is important that every organization does all it can to combat these criminals and being informed is a key element. In this article we see the…
 Giacomo Lanzi
Giacomo Lanzi
Acronis Active Protection: defense against ransomware
Acronis Active Protection is an advanced anti-ransomware technology. It actively protects all the data on your systems: documents, data of all kinds and Acronis backup files. It is a technology available for Windows and Mac OS X operating systems and protects against the latest ransomware actions such as Petya, WannaCry, Locky and Osiris. What is Ransomware? Ransomware is a particularly…
 Alessandro Stesi
Alessandro Stesi
Corporate backup solutions Self-protection tests
Introduction Corporate backup solutions: In light of the growing number of ransomware attacks in which cryptolockers stop database processes to unlock database files for encryption (Cerber, GlobeImposter, Rapid, Serpent) and they can encrypt local and network backups to request a ransom payment (Rapid, Spora), we decided to test the self-protection capabilities of the best backup solutions used in the corporate…
 Alessandro Stesi
Alessandro Stesi
[Name change] Acronis Data Cloud –> Acronis Cyber Cloud
As you know, Acronis Data Cloud will receive a host of essential new enhancements (like backup for G Suite and cryptomining protection) and be renamed Acronis Cyber Cloud in just a few weeks. Acronis Cyber Cloud: distinguishes our data protection solution because it speaks to the customer’s weaknesses. ♦ Offering next-gen data protection – cyber protection – meets…
Modern Data Protection: The Difference is in the Cloud
Modern Data Protection How to Completely Safeguard Businesses – with Ease Simplify is often a valuable mantra of success. Yet in a complex and ever-evolving IT environment, it isn’t necessarily the go-to approach for service providers. In the case of data protection, simplification may not only seem unlikely, but potentially unwise. Fortunately, certain innovative cloud technologies now make it simple…
 Alessandro Stesi
Alessandro Stesi
Subscription business model – Basics
subscription Subscription is a convenient way to receive updates, products or services on a regular and ongoing basis. This business model has stood the test of time. Over the years, satisfied customers have used regular services by subscribing news, magazines, CDs, wine and even opera tickets. And then the cloud arrived. The cloud has made IT complex easy and cheap,…
 Piergiorgio Venuti
Piergiorgio Venuti
New Acronis Cloud Backup model for end users and new reseller plan
New Acronis Cloud Backup model for end users and new reseller plan Our Acronis Cloud Backup service is renewed with two distinct subscription types for end users and retailers / system integrators. With the former, it is possible to meet the needs of small and medium businesses that need to have a professional solution for managing their local and…
 Piergiorgio Venuti
Piergiorgio Venuti
A Hybrid Cloud Backup Solution for System Integrator and reseller
ACRONIS CLOUD BACKUP SYSTEM INTEGRATOR Thousands of system integrator — from small to large — succeed by selling an award- winning backup-as-a-service solution that supports more than 20 platforms. Acronis Cloud Backup protects any virtual, physical, and cloud environment, and lets you quickly realise incremental revenues with zero upfront costs and a pay-as-you-go business model. PROTECT ANY WORKLOAD, BACKUP TO ANY STORAGE…
 Piergiorgio Venuti
Piergiorgio Venuti
Alternative to the NAS
NAS Network Attached Storage (NAS) is a great low-cost tool for storing your data like backups (single files / folders or entire operating system images). Thanks to its connection (ethernet or wifi) with the local network (LAN) it is possible to easily copy the contents from your PC or server to the NAS using manual and / or automatic systems….
 Piergiorgio Venuti
Piergiorgio Venuti
Stay in control of your fast-moving, quick-shifting data
At the breakneck speed of business, it can be easy to lose control of your data as it races between your physical and virtual servers, PCs and mobile devices, and private and public clouds. And as every racing fan knows, speed is paramount, but speed without control can be disastrous. [btnsx id=”5010″] With better control, you can more safely manage…
 Piergiorgio Venuti
Piergiorgio Venuti
7 motivi per NON rinnovare un backup tradizionale
Veeam Availability Ogni giorno sempre più clienti dei backup tradizionali passano a Veeam®. Perché? Perché le tecnologie progettate per l’era client-server non possono offrire l’Availability 24.7.365 di cui necessitano le aziende moderne, né la capacità di ripristinare in pochi minuti o secondi qualsiasi servizio IT in esecuzione nel cloud ibrido. [bg_collapse view=”button-blue” color=”#ffffff” icon=”eye” expand_text=”Maggiori informazioni” collapse_text=”Mostra meno” ] La sostituzione…
 Piergiorgio Venuti
Piergiorgio Venuti
Remote access for MSPs in Veeam Backup & Replication 9.5 Update 2
Veeam Backup Remote Access. We are happy to announce that the RTM build of Veeam Backup & Replication 9.5 Update 2 is now read up and running on Veeam Cloud Connect service! This is the latest update for our flagship product and adds support for the upcoming release of Veeam Agent for Microsoft Windows 2.0 along with other significant enhancements…
 Piergiorgio Venuti
Piergiorgio Venuti
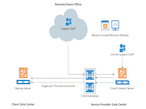
Two ways to implement your BaaS (Backup as a Service)
BaaS (Backup as a Service) is the service that allows your company to save a copy (off-site copy) of data in Cloud. In this way, you can store your information in a safe place and then restore it at any time in case of disaster.BaaS is one of the ways to implement backup 3-2-1 rule. Secure Online Desktop provides its…
 Piergiorgio Venuti
Piergiorgio Venuti
BaaS with Veeam Cloud Connect
Veeam 2017 Availability Report 3 Steps To Avoid $21.8M In Downtime Costs [btnsx id=”4150″] Examining the real world impacts when service Availability goals are not met. Veeam® commissioned ESG to survey over 1,000 global IT decision makers to better understand the protection, recovery, and Availability challenges they are facing today. Overall results were surprising – demonstrating a startling amount of…
Customers
Twitter FEED
Recent activity
-
SecureOnlineDesktop
Estimated reading time: 6 minutes L'impatto crescente delle minacce informatiche, su sistemi operativi privati op… https://t.co/FimxTS4o9G
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The growing impact of cyber threats, on private or corporate operating systems… https://t.co/y6G6RYA9n1
-
SecureOnlineDesktop
Tempo di lettura stimato: 6 minuti Today we are talking about the CTI update of our services. Data security is… https://t.co/YAZkn7iFqa
-
SecureOnlineDesktop
Estimated reading time: 6 minutes Il tema della sicurezza delle informazioni è di grande attualità in questo peri… https://t.co/tfve5Kzr09
-
SecureOnlineDesktop
Estimated reading time: 6 minutes The issue of information security is very topical in this historical period ch… https://t.co/TP8gvdRcrF
Newsletter
{subscription_form_1}© 2024 Cyberfero s.r.l. All Rights Reserved. Sede Legale: via Statuto 3 - 42121 Reggio Emilia (RE) – PEC [email protected] Cod. fiscale e P.IVA 03058120357 – R.E.A. 356650 Informativa Privacy - Certificazioni ISO












